ZIP File Password Recovery
Encrypted ZIP Removal
Removal of a password from an encrypted zip file can be easy or hard depending on the complexity of the password. Using a tool such as John the Ripper you can break out the password by matching the computed hash at a rate of millions of attempts per second. So a strong password should be used to ensure security of the file.
Recovery of the password can be achieved by retrieving the hash from the document and matching the hash against calculated hashes of known strings. This is a similar methodology to that used in cracking other hashes such as MD5 password recovery, SHA1 password recovery or even Microsoft Office document password recovery (Word doc / Excel xls).
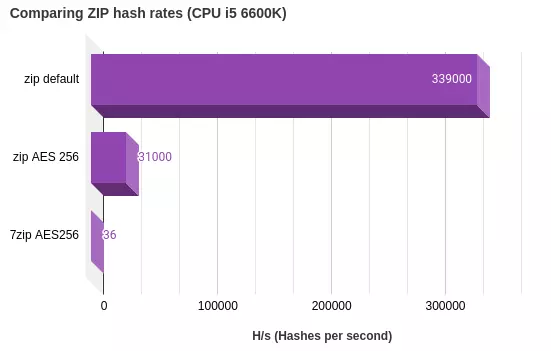
The standard format for an encrypted zip file uses the ZIP2.0 format. This is not very secure as shown in the chart below and can be cracked using standard tools. Another method is the AES encryption first introduced by WinZIP and available in some software such as WinZIP and 7zip. The AES encrypted zip archive is much more difficult to crack open as the complexity of the computation is simply more difficult - making the cracking time significantly longer.
Try our ZIP password recovery tool here, to attempt to crack the password of an encrypted zip file.
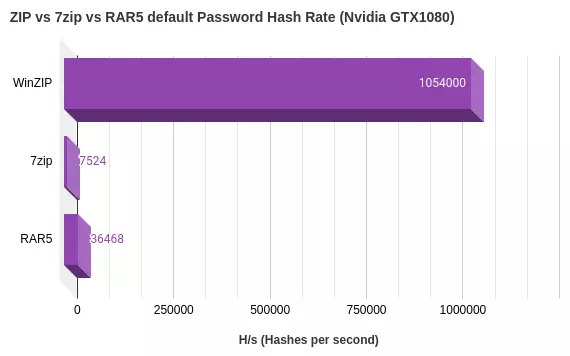
Benchmark ZIP File Cracking (i5 CPU vs Nvidia GTX1080)
Using Hashcat Password Tool or John the Ripper to crack the zip file is the best bet. These tools can use high speed graphics processing chips (GPU) to crack the hashes faster than your even the fastest of CPUs. Even using cutting edge GPUs these passwords are difficult to recover as the algorithm is one of the strongest used in when compared to other standard document or file encryption algorithms.
In this chart it is clear to see the simplicity of the legacy ZIP 2.0 standard when compared to the AES encrypted zip file. The slower attack time for the 7zip encrypted AES file is due to the use of multiple iterations of the AES256 calculation in the 7z format.
Cracking ZIP file with Password
John the Ripper (a password recovery program) comes with a utility called zip2john that is used to extract the encrypted hash from the file.
1. Extract the Hash from the zip
Using zip2john a utility packaged with John the Ripper we can extract the zip file hash. With the hash we can use either John the Ripper or Hashcat to attack the hash to find the password.
user@host:~$ zip2john test.zip
ver 1.0 efh 5455 efh 7875 test.zip/test.txt PKZIP Encr: 2b chk, TS_chk, cmplen=17, decmplen=5, crc=3BB935C6
test.zip/test.txt:$pkzip2$1*2*2*0*11*5*3bb935c6*0*42*0*11*3bb9*7ea9*f0728c57843209fbe14dcf4f7f46661068*$/pkzip2$:test.txt:test.zip::test.zip
Depending on the zip compression program used the strength of the cipher and format of the zip2john output may be different to what you see in the example above.
2. John the Ripper and ZIP Files
This hash is the key to the file. When attacking the file in an effort to “crack” the password you use this hash to try and find a matching known string.
By attacking the hash it saves you having to type passwords into zip file password prompt thousands of times!
john will detect the format of the hash and start checking for passwords using a simple command line as shown below.
user@host:~$ zip2john test.zip > test.hash
user@host:~$ john test.hash
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 4 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Warning: Only 3 candidates buffered for the current salt, minimum 8 needed for performance.
Warning: Only 7 candidates buffered for the current salt, minimum 8 needed for performance.
Warning: Only 3 candidates buffered for the current salt, minimum 8 needed for performance.
Almost done: Processing the remaining buffered candidate passwords, if any.
Warning: Only 5 candidates buffered for the current salt, minimum 8 needed for performance.
Proceeding with wordlist:/snap/john-the-ripper/current/run/password.lst, rules:Wordlist
password (test.zip/test.txt)
1g 0:00:00:00 DONE 2/3 (2022-01-14 11:08) 20.00g/s 606380p/s 606380c/s 606380C/s 123456..ferrises
Use the "--show" option to display all of the cracked passwords reliably
Session completed
Using a custom wordlist with John is a simple command line argument.
user@host:~$ john test.hash -wordlist=rockyou.txt3. Hashcat and ZIP Files
As with the john example above we first need to extract the hash from the file. Use zip2john the same as above. Then redirect to a file and edit the file to remove the first characters up to to first $. The file should like the example below.
$pkzip2$1*2*2*0*14*8*db5c50fc*0*46*0*14*db5c*59b2*1d8f608cc212d947bee8bdf5eefc17d78392af66*$/pkzip2$:test-txt.txt:test-zip-weak.zip::test-zip-weak.zip
Now we will use hashcat to try and guess the password for this hash. There are a number of formats for zip2 / pkzip etc. Depending on the program used to encrypt you may need to try different hashcat modes.
hashcat --help | grep -i zip will show the modes for the different formats. Note that you should be using hashcat 6.1+ or a more recent version to ensure you are maximising your password cracking capability.
In the example test.john is the file that contains the zip file hash extracted using the zip2john utility.
(vagrant㉿kali)$ hashcat -m 17210 test.john rockyou.txt
hashcat (v6.1.1) starting...
OpenCL API (OpenCL 1.2 pocl 1.6, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==========================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i7-6700 CPU @ 3.40GHz, 2884/2948 MB (1024 MB allocatable), 2MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers applied:
* Not-Iterated
* Single-Hash
* Single-Salt
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 64 MB
[s]tatus [p]ause [b]ypass [c]heckpoint [q]uit => Dictionary cache building roDictionary cache built:
* Filename..: rockyou.txt
* Passwords.: 14344392
* Bytes.....: 139921507
* Keyspace..: 14344385
* Runtime...: 1 sec
$pkzip2$1*2*2*0*14*8*db5c50fc*0*46*0*14*db5c*59b2*1d8f608cc212d947bee8bdf5eefc17d78392af66*$/pkzip2$:password
Session..........: hashcat
Status...........: Cracked
Hash.Name........: PKZIP (Uncompressed)
Hash.Target......: $pkzip2$1*2*2*0*14*8*db5c50fc*0*46*0*14*db5c*59b2*1...kzip2$
Time.Started.....: Wed Feb 9 21:00:25 2022 (0 secs)
Time.Estimated...: Wed Feb 9 21:00:25 2022 (0 secs)
Guess.Base.......: File (rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 33625 H/s (0.16ms) @ Accel:1024 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 2048/14344385 (0.01%)
Rejected.........: 0/2048 (0.00%)
Restore.Point....: 0/14344385 (0.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: 123456 -> lovers1
Started: Wed Feb 9 21:00:01 2022
Stopped: Wed Feb 9 21:00:27 2022
The password list used is the rockyou.txt dictionary. You can see from the output we achieved about 33000 hashes per second using an i7-6700 CPU. Not great, we would definitely want to use a GPU for a serious password attack.
Password Protect Files on Windows and Linux
Password protect ZIP file in Windows
Windows comes with a builtin ability to extract and compress files using the ZIP format. These will be accessible using other third part ZIP extract programs on Linux, Windows or Mac based systems. However, there is no option to add a password to the zip file on Windows using the default functionality. You can encrypt the file using builtin encryption tools but this is not the same as the standard ZIP file password protection. To do this we will need to use a third party program such as WinZIP, 7zip or WinRAR.Password Protect ZIP File with Ubuntu using Command Line
Using the standard zip program in Ubuntu Linux we can add a password to a newly created zip file very easily. If the command line zip is not installed use the apt install command and then run the following. You will be prompted for the password.
user@test:~/$ sudo apt install zip
user@test:~/$ zip -e myzip.zip myfile.txtAlternatively there is an open source version of 7zip that can be installed from the Ubuntu package manager.
user@test:~/$ sudo apt install p7zip
user@test:~/$ 7za a -tzip -p -mem=AES256 myzip.zip myfile.txt