The version of Office used greatly affects the ability to crack the hash. Later versions of Microsoft Office are very difficult as they use a much stronger algorithm to protect the document. Earlier releases are easily cracked through the weak algorithms used.
Microsoft Office Password Recovery
Word / Excel / Powerpoint
Microsoft Office Document Password Recovery Password recovery (cracking) of protected Office documents such as Word (doc/docx) or Excel (xls/xlsx) can be achieved by simply guessing the password. No this is not a joke. Guessing the password is the only way to crack the hash. However, you can do better than typing in thousands of passwords by hand. Using password recovery tools such as John the Ripper (jtr) or Hashcat simple passwords crumble when attacked.
Try our free online password recovery tool below to quickly determine if a password protected document has a weak password. The number of attempts at recovering the passwords will depend on the version of Microsoft Office the document was saved in. The number of passwords tested will be millions for older versions of Office such as Office 97/2003 or only a few thousand in later versions of Microsoft Office 2013 / 2016.
When recovery of a password can affect the businesses bottom line it pays to have an understanding of the art of password recovery. Whether you work in Cyber Security or are an IT support professional, a bit of knowledge about passwords and recovery will go a long way.
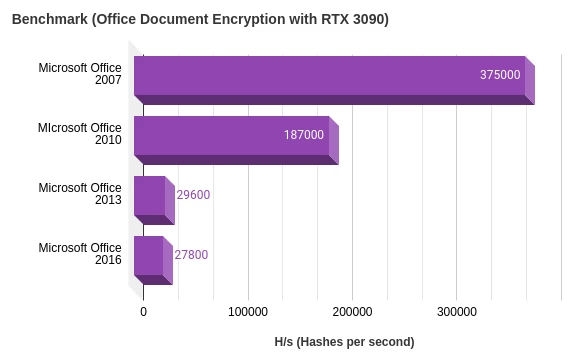
Benchmark Microsoft Office Password Cracking with Hashcat (RTX 3090)
In this chart it is clear to see the version of Microsoft greatly affects the hash rate when attacking passwords generated for these documents.
Password recovery has a wealth of jargon that can mean the same thing or very different things depending on the password breaking technique being used. Decrypting, decoding and brute forcing are all different ways that a password can be attacked. In the end the correct technical phrase does not matter when you just want to get the password to your locked up XLS budget!
Test password protection in documents including Microsoft Office 2016, 2013, 2010 and more. Depending on the version we will test thousands or even millions of possible passwords in a matter of seconds.
Password Recovery of Microsoft Office Documents using John the Ripper
Using John the Ripper to find the password of an Office Document is a relatively straight forward process. It involves first extracting the hash using a script that is actually bundled with John the Ripper (jumbo community edition). Note that the John the Ripper version should be the Jumbo version to have the included scripts for extracting password hashes.
test@ubuntu:~$ office2john.py Documents/test-pass3.doc
test-pass3.doc:$oldoffice$1*0b50d48778cc821e2ee5487440fc2cde*c0f65e3c31f106f5e219991ef698e9c2*83d1be759884b408852b49663ca64436:::::Documents/test-pass3.doc
To use the hash for the test-pass3.doc we need to redirect it to a file so that john can read the hash from the file. See the steps below to extract the hash to a file and then run john against that file using the default cracking method.
test@ubuntu:~$ office2john.py Documents/test-pass3.doc > test-pass3.hash
test@ubuntu:~$ john test-pass3.hash
Using default input encoding: UTF-8
Loaded 1 password hash (oldoffice, MS Office <= 2003 [MD5/SHA1 RC4 32/64])
Cost 1 (hash type [0-1:MD5+RC4-40 3:SHA1+RC4-40 4:SHA1+RC4-128 5:SHA1+RC4-56]) is 1 for all loaded hashes
Will run 4 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, 'h' for help, almost any other key for status
Almost done: Processing the remaining buffered candidate passwords, if any.
0g 0:00:00:00 DONE 1/3 (2022-03-01 22:18) 0g/s 142568p/s 142568c/s 142568C/s Doctest1900..Dpass31900
Proceeding with wordlist:john/run/password.lst
Enabling duplicate candidate password suppressor
password' (test-pass3.doc)
1g 0:00:00:01 DONE 2/3 (2022-03-01 22:18) 0.8547g/s 338229p/s 338229c/s 338229C/s 032892..winner17
Use the "--show --format=oldoffice" options to display all of the cracked passwords reliably
Session completed.
We can see here that john discovered the password with the default password.lst used by JtR.