Libre (Open) Office Password Recovery
Open Document Format
Libre Office (Open Office) uses the Open Document Format (ODF) for saving files. Password protection can be added to these documents using the built in encryption option. Recovering ODF passwords is not a simple matter as the encryption algorithm used for Open Office documents is quite strong.
Recovery of the password can be attempted by retrieving the hash from the document and matching the hash against calculated hashes of known strings. This is a similar methodology to the more basic hashing used in other hashes such as MD5 & SHA1. Microsoft Office Document have a similar option to encrypt the document; password recovery is then a similar process (Word doc / Excel xls).
The same encryption is used for different types of Open Office document including Writer (odt), Calc (ods), Impress (odp) and Draw (odg). However, there may be a slight variation in the encryption process depending on the version of Libreoffice.
Using a known list of passwords we can calculate hashes and attempt to recovery the password. Try our Libre Office password recovery tool here, to attempt to crack the password of an encrypted document.
Benchmark Libre (Open) Office Password Cracking with Hashcat (RTX 3090)
Using CudaHashcat Password Tool or John the Ripper to crack the Open (or Libre) Office document password is the best bet. These tools can use high speed graphics processing chips to crack the hashes faster than your even the fastest of CPUs. Even using cutting edge GPUs these passwords are difficult to recover as the algorithm is one of the strongest used in when compared to other standard document or file encryption algorithms.
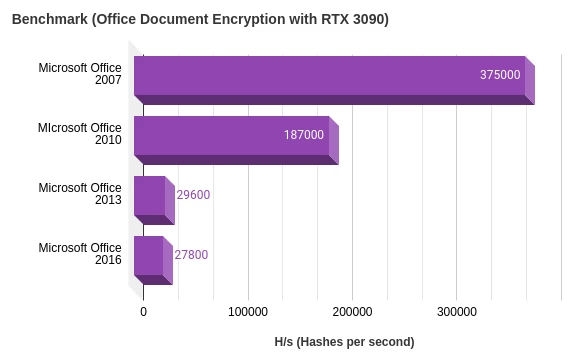
In this chart it is clear to see the version of Microsoft greatly affects the hash rate when attacking passwords generated for these documents.
Password Recovery of Libre Office (openoffice) Documents using John the Ripper
Using John the Ripper to find the password of an Office Document is a relatively straight forward process. It involves first extracting the hash using a script that is actually bundled with John the Ripper (jumbo community edition). Note that the John the Ripper version should be the Jumbo version to have the included scripts for extracting password hashes.
test@ubuntu:~$ libreoffice2john.py test-pass.odt
test-pass.odt:$odf$*1*1*100000*32*a91ae45112bf9ad739e722982bc8b092a75d4b0108c5f180ca469e4ff7a1bd13*16*4ff28cbf2279736430b55a5376930493*16*7be293aafe34d815d113ef0f4321316a*0*5343fe1fcb77665901ec5817d7cfb9f3ec33d6d6b6063c454daece039129066a5c8dd6c905c35d1975ff1fc8a3af479f9c068a0e1120593267e18688250c715fa8cedd4b90660130dd5dab15f58b9e4bc906d76f21bc8aae374010bc4ffc6d292801b5caf506cb57014f046c221df5c436ff4d28fdaa49a8645367b1fd388f31e09f30c42de0607ec7b3551e6bea3af1cd6cfff0ccad641bff16d66fe824183f2a387925d24861d414e462639ba3d4ae81fea588775d506d766ed9028561c27905400771d50a16bc92e398de1ffc14443e515f25f4ccd7c269915e2e0ec92eae22931b393bed8166ff40d2582d5de5bcb1ebfdf8670648a5c5cb1487adaecb4c48db40a8224cf18089afff518c1169f2fd6e2bf62cdde3f8152cd94bb97935cd47494fbd3bac03c59c9bc20c0b1217c941f8e604533bc7712aaf9e03fd09cdeba047ffd0e076c7ae7d9ef8a1ed650ee8c4ea6793da45005362969338e22cbbbc50a0b03db030dd65e98bb63952b6a66614a923c97cf9803c827d13a774c71fcf82bd44405c83991ecf649e73fc66ee713957bcf620774feaf63782666c51de95db205afa6d49e788d2780e1f6a753f42d801ad048aaca1ddf2c8fec914e1da3495f75d34d67752575c8f3c26ef45f79b2f95f0164ad576883e263530ded44a97ad895db6a7cf2a1381b0970781a45f6d5a97f8059c6063ed7dd742985395037fe82c5aa83d921466463ed8395ec374ce962a87e27800b673e9a9796b5d7614be50c25de132eef4cd2f88ed4a525cc29cfca30b4f1b8637d952f8192158283e27e8408d8f01e11cf3566c041d24c81891e6416b0c0df27e93252f15170368bfd39a3c200032a50b0afc93703724d4e5513e6fafd5e6fade1d07eebccdfda323774e38610958239cc610789273eae3a5b2f29388b53ae0bb165ec9e8cba0d2449064490943e03da58821dddfe1e3b87e8532cb0a39315d22f4c30795b4d9fa1ce261c2c5e28172564fc942dac11568f38ecf7201f1c738766100e6f5ac3c8e351241e2f598e6ad0bf121e27d03f656317d0052985ab5de4182709a362be21dd00d5c9ba469fada26e07299172bd977d9c386e8e8a986dc63c2440e21a42eb7951c53e9a080370344cf2b81df226e7a8579eb9a87328f37e3c6fa02f86c8a45e399305b6a41c9517c936d7a869edb4642bf842aff37234f644c5973af7b5a9ca471bc594f949f2f28d3f774a3cfa9e2663d03a0c1311d76033c048cea16c11f01ff3c5dbdb3eabe9c08b17383601194d310068e37a8454477ec44427181456153d9d7c25b84018a6a70e505b0d891a5efe30c9e0c3fa2c3d205462dbb3c7f8a3b7cdbe44097a20692250cf1096bf5203ecb0b380d97c6ac66c0b1499dcf8cc499488c64b4a43a854494b704bab3f5246cedf51f45d5c0ffa6a2237877da702ba44c:::::test-pass.odt
To use the hash for the test-pass.odt we need to redirect it to a file so that john can read the hash from the file. See the steps below to extract the hash to a file and then run john against that file using the default cracking method.
test@ubuntu:~$ libreoffice2john.py test-pass.odt > test-pass.hash
test@ubuntu:~$ john test-pass.hash
Using default input encoding: UTF-8
Loaded 1 password hash (ODF, OpenDocument Star/Libre/OpenOffice [PBKDF2-SHA1 256/256 AVX2 8x BF/AES])
Cost 1 (iteration count) is 100000 for all loaded hashes
Cost 2 (crypto [0=Blowfish 1=AES]) is 1 for all loaded hashes
Will run 4 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, 'h' for help, almost any other key for status
0g 0:00:01:26 86.57% 1/3 (ETA: 22:28:10) 0g/s 260.0p/s 260.0c/s 260.0C/s Tpass2009..Ttest-pass.odt2010
Almost done: Processing the remaining buffered candidate passwords, if any.
0g 0:00:01:42 DONE 1/3 (2022-03-01 22:28) 0g/s 259.6p/s 259.6c/s 259.6C/s Odtpass1901..Opass1900
Proceeding with wordlist:john/run/password.lst
Enabling duplicate candidate password suppressor
0g 0:00:03:52 0.00% 2/3 (ETA: 2023-05-21 11:57) 0g/s 261.6p/s 261.6c/s 261.6C/s 03011987..starstruck
0g 0:00:04:15 0.00% 2/3 (ETA: 2023-04-21 17:41) 0g/s 261.7p/s 261.7c/s 261.7C/s southampton..northwest
Password12345 (test-pass.odt)
1g 0:00:07:18 DONE 2/3 (2022-03-01 22:33) 0.002279g/s 261.6p/s 261.6c/s 261.6C/s 031990..100805
Use the "--show --format=ODF" options to display all of the cracked passwords reliably
Session completed.
We can see here that john discovered the password with the default password.lst used by JtR. Note that the password attempt rate was around 260 passwords per second. When we did a similar test on the old Microsoft Office Document we were hitting 330000 passwords per second.